How your secure data is being targeted every day.
The steps you can take to protect your system:
When you have something of value, like secure data, it seems someone else always wants to obtain it for themselves or prevent you from leveraging it for your own benefit. That’s why cyberattacks are a constant challenge for hardware and software architects. In this first of a series of blogs, we provide an overview of the targets, the attacks, and the shields that you need to be aware of when transmitting, storing, and using valuable data.
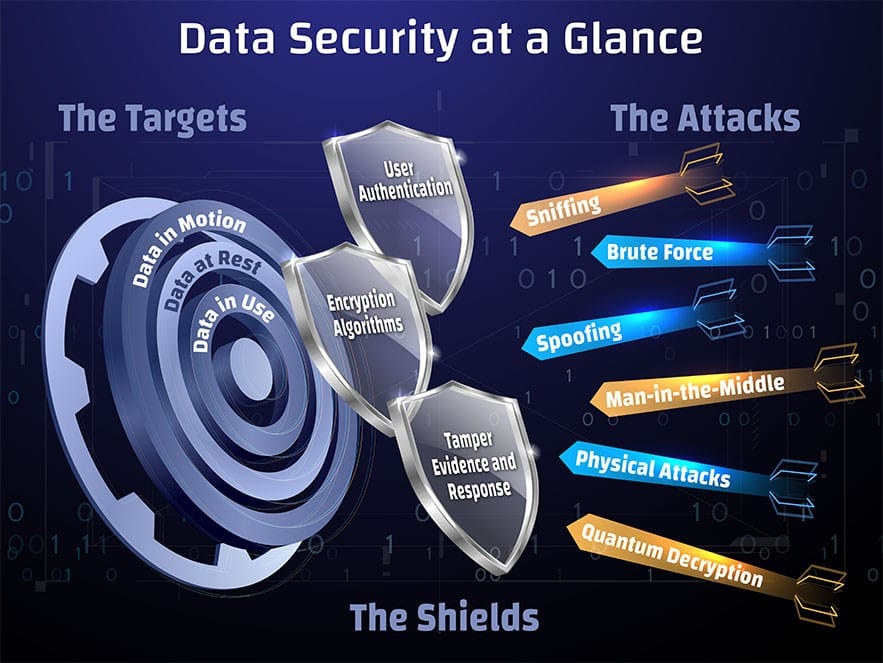
The targets
There are three principal areas that hackers target to compromise your systems and data.
Data in Motion: When information is being communicated between systems, it is called Data in Motion. Think of IP packets moving across a network or a wireless sensor transmitting information to a system. Data in Motion is the easiest digital data to acquire because the end systems do not have control over the data or what has access to it while it is physically moving between systems.
Data at Rest: Information that is stored in one location like a hard drive, flash drive, SD card, or other storage media is called Data at Rest.
Data in Use: Information that is currently being used in a system is known as Data in Use. It could be data stored in RAM, swap space, buffers, or registers. When an application that handles sensitive information is running, data could be targeted in the RAM while it is being processed.
The attacks
Computer security engineers not only need to watch out for individual cyberattacks, but they also need to protect from attacks used in combination — like a one-two punch in a boxing match. Below are just a few examples of cyberattack methods.
Sniffing: A basic, passive attack on Data in Motion is sniffing. When a successful sniffing attack captures data, it can be turned into a more active attack by sending information to the same victim in an attempt to replay and capture the conversation.
Brute force: Brute force attacks are the software equivalent of using a sledgehammer to hit a door as many times as necessary to break through. Fortunately, the good guys can make these doors almost impenetrable through encryption. This active attack is typically carried out on Data at Rest due to the time necessary to calculate and process decryption algorithms. Despite its intimidating name, brute force is one of the weakest attacks your systems can face, but still must be protected against. When you properly implement encryption protocols, your risks from this attack are minimal.
Spoofing: In a spoofing attack, someone is directly impersonating one end of a conversation. It is frequently the direct result of other successful attacks, such as sniffing or man-in-the-middle. Because an attacker doesn’t know how to impersonate an endpoint, they will listen to a data conversation using sniffing. Once they get the information they need, they can use spoofing to impersonate the endpoint and take over. When a credentialed transaction is intercepted over a secure network and then replayed to the same system to gain access, this is called a replay attack. This sub-type of spoofing is especially dangerous because the hacker doesn’t even have to decrypt the message to gain access. To protect against a replay, both the sender and receiver should establish a random session key, which is only valid for one transaction and can’t be used again.
Man-in-the-middle (MiTM): In this active attack, bad actors surreptitiously insert themselves between two parties who believe they are communicating directly with each other, with the goal of intercepting, altering, or controlling the conversation. MiTM attacks can be prevented by taking a zero-trust approach to security. Therefore, many cryptographic protocols include some form of endpoint authentication, which allows a chain of trust to be built, so the system can verify that a message comes from a genuine source. MiTM is easiest to execute on data moving over a network (Data in Motion), because that information is easiest to intercept and alter.
Physical attacks: All cyberattacks aren’t performed through software or from remote locations. Secure data can also be compromised by attackers physically gaining access to or manipulating your hardware through a variety of techniques — opening cases, x-raying hard drives, measuring signals, and manipulating voltages. One example of a physical attack on microcontrollers is to lower their voltage input to thresholds that block execution of firmware. An attacker using this method can cause the controller to skip critical sections of code, such as authentication steps, if other safeguards aren’t implemented.
When your hardware is your security boundary, you want to be notified if it’s been tampered with. New responsive technologies are also being developed that will allow hardware systems to take action when tampering is detected — such as automatically wiping encrypted Data at Rest.
Quantum decryption: A looming threat to cryptographic systems is Shor’s algorithm being run on quantum computers. This algorithm reduces the amount of effort for a brute force attack to break elliptic curve encryption. Cybersecurity experts have been preparing to combat this capability. Even though capable quantum computers are many years away, the NSA has estimated quantum-resistant encryption standards will be available in 2024.
The shields
User authentication
When planning to protect data, you first need to consider your trust architecture for your unique system. This trust architecture will define how users are authenticated. What are your roots of trust? How do you build a chain of trust? How do you protect the trusted parts of your system? And then how do you extend that chain of trust to external devices or systems? If you’re taking a zero-trust approach and you want to communicate between two servers, how do you enable that communication? These are all questions that need to be answered when choosing your security protections.
Encryption algorithms
Symmetric vs. Asymmetric vs. Hashing
Most industry experts are familiar with symmetric encryption that uses one secret key to both encrypt and decrypt information. Imagine we have one system named Bob and another system named Alice. Bob has secure information he wants to share with Alice, so he uses a secret key to encrypt it before sending. Alice uses the same shared key to decrypt the information. This works great until someone else intercepts the key. In this case, Bob and Alice’s information is no longer secret, and every other system that uses the secret key would also be compromised. This approach is less secure, but it is also less resource intensive than asymmetric encryption, so it’s typically used to encrypt large amounts of data.
With asymmetric encryption, there are two keys. One key is private or secret and is never known to anyone outside of the person who owns it. And then the other key is public and can be distributed to anyone freely. Anything encrypted by one key can only be decrypted by the other. That means Bob and Alice can still share secure information even though they don’t share the same key. Asymmetric is generally used to either authenticate external devices or to exchange encryption keys for symmetric encryption.
Hashing scrambles data into something unreadable, but it is repeatable with the same inputs. The unreadable output is typically referred to as a digest. It is typically used as a signature or as a unique index.
Each encryption method has advantages and disadvantages. They are chosen based on the level of trust required and the type of information being encrypted.
NSA-approved algorithms
The National Security Agency (NSA) developed the Commercial National Security Algorithm suite (CNSA) for encrypting secure data up to the top secret level.
- Advanced Encryption Standard (AES) Algorithm: Based on the Rijndael cipher, AES is a symmetric encryption algorithm. AES employs 128-, 192-, or 256-bit variants based on the security level needed and processing power required. You would use AES when you are encrypting large amounts of information and when you are able to securely share a secret key.
- Secure Hashing Algorithm (SHA-2): SHA-2 shortens input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions. The only difference between hashing and encryption is that hashing is one-way, meaning once the data is hashed, the resulting hash digest cannot be cracked, unless a brute force attack is used.
- Elliptic Curve Diffie-Hellman (ECDH) and Elliptic Curve Digital Signature Algorithm (ECDSA) with curve P-384: These asymmetric algorithms allow user authentication and secure encrypted exchange of information. Security of elliptic curve algorithms relies on the practical difficulty of finding the curve of a random ellipse even while knowing one of the base points. You use ECDSA when you want to authenticate systems using their public key. You use ECDH when you want to securely exchange a secret.
- RSA: As one of the oldest encryption methods in the CNSA suite, RSA is an asymmetric algorithm that is widely used to secure data transmission. The security of RSA relies on the practical difficulty of factoring the product of two large prime numbers, known as the “factoring problem”. There are no published methods to defeat the system if a large enough key is used. RSA is often used to transmit shared keys for symmetric-key cryptography, which are then used for bulk encryption-decryption.
Encryption solutions
Here are some of the more well-known implementations of data encryption.
- NSA Type 1 Encryption: Type 1 encryption is the most secure way to protect classified and secret information. Because it uses a stringent certification process, it is also the most difficult and expensive to implement. Every time a company must make a change to a product, they must also get recertified. So, it’s more difficult to make updates. With ever-increasing throughput requirements of data interfaces, Type 1 Encryption has difficulty keeping up with industry demands for high speed ethernet and video applications.
- Commercial Solutions for Classified (CSfC): CSfC relies on layers of commercial encryption solutions to achieve similar security to the single-layer NSA Type 1 standard. NSA has developed, approved, and published solution-level specifications called Capability Packages (CPs) and works with technical communities from across industry, government, and academia to develop, maintain, and publish product-level security requirements called Protection Profiles (PPs). These NSA-certified solutions could include VPNs, Federal Information Processing Standards (FIPS) hard drives, and end-to-end encryption.
- Crypto Ignition Keys/Key Fill: These devices are used to enable the cryptographic functions of systems with Data at Rest or Data in Use. They prevent the need to store cryptographic keys on a system, allowing separate physical storage or generation on the fly.
Tamper evidence and response
Tamper evidence has been available on physical hardware systems for many years. It may be as simple as a seal being broken to indicate someone has accessed a box, or a notification that a secure message may have been intercepted or altered. The next step is developing tamper-responsive systems that have the ability to erase encrypted data in the event of a breach. This approach proactively prevents access to secure data by zeroizing crypto keys and sanitizing Data at Rest or Data in Use.
Next steps
When it comes to cyberattacks one thing is certain: Nefarious forces will always be looking for ways to get around the protections we put in place. That’s why we continue to advance the security of our rugged hardware by developing new technology to ensure our customer’s data and communication stays private.
In this article, we touched on the types of data that are targeted by cyberattacks and the protections available today. Explore our complete series of articles about cybersecurity to learn more details about protecting Data in Motion, Data at Rest, Data in Use, as well as encryption and tamper security.