What is Data in Use? Use it or lose it.
As the adage goes, you have to use your data correctly with the appropriate encryption protections, or you risk losing the data you’ve worked so hard to gather. To deal with this challenge, let’s start with the basics. Information that is currently being used in a system is known as Data in Use. It could be data stored in RAM, swap space, buffers, or registers. To learn more about protecting this temporarily stored data, let’s return to the network scenario we introduced in our Data in Motion blog and our Data at Rest blog.
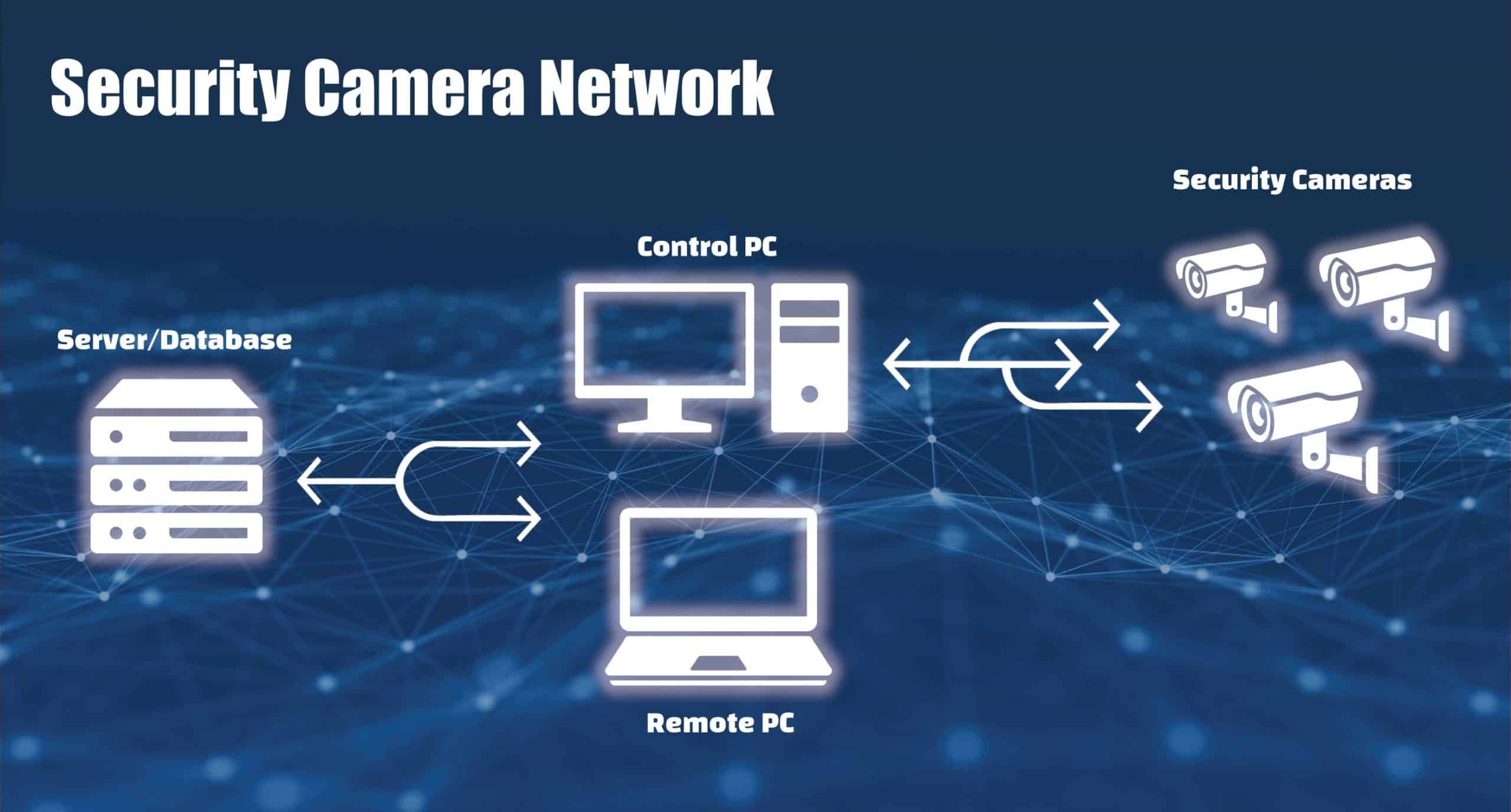
Security camera network
Our example company has implemented a security camera network to help monitor a restricted portion of their property. Video feeds are stored on onsite computers. All the camera footage is also stored in a database on an off-site server, and users can view the logged footage remotely using an authorized computer on the network.
Our final area of focus for our example security camera network is Data in Use. This temporarily stored data doesn’t have the vulnerability of being accessible outside the system like Data in Motion. Nor does it have the vulnerability of permanence like Data at Rest. So why does it need to be protected? Data in Use is important because it’s the information your system is currently using. Running applications require storing configuration information and/or information to allow program execution. When an attacker alters the configurations or information that an application depends on, it can have serious consequences on the behavior and security of the system.
Why do attackers target Data in Use? Because its useful data.
Vulnerabilities:
- Other programs on the system
- Social engineering
- Successful attacks can be hard to detect
Goals of attackers:
- Altering configuration information
- Obtaining sensitive information such as keys/credentials
- Bypassing authentication
- Holding systems for ransom
How do I protect Data in Use? Be vigilant at every step.
In our example, Data in Use is the data being used in the server database, control PC, remote PC, and security cameras. It’s important to keep in mind that an attacker normally has to have access to the system in one way or another — whether it is direct physical access or through installing malicious software via phishing or other means. The best protection for Data in Use is ensuring attackers don’t have access to your system and keeping security best practices in mind while using your system to avoid the installation of malware.
Social engineering: email or text message manipulation.
Attackers often use social engineering tactics because it is easier to exploit the inclination to trust other people than it is to hack software. For example, it takes much less time to send an email to trick someone into giving you their password than the effort you might spend trying to hack a password. So, when you get an email from somebody you don’t recognize, examine it carefully before you proceed. Be suspicious of emails that claim you must click, call, or open an attachment immediately. If an email or text message looks like a scam, it probably is.
Code injection: digital misdirection.
Code injection attacks are when an attacker changes a program’s execution code to do something different. This alteration of the program’s behavior may allow the attacker to skip portions of the program (such as authentication steps), or even jump into another program’s memory. A basic example of this is a buffer overflow, where an attacker can overwrite memory by entering a larger value than expected into an input field. In our security system example, an attacker that is able to inject code into the server database could lock up the application that is logging the camera feeds, preventing the information from being stored. To protect against code injection, we recommend you use memory enclaves as a form of user authentication. You should perform thorough testing during software development and use hashing algorithms to verify the contents of your memory enclaves.
Privilege escalation: hey, you shouldn’t be here!
A privilege escalation attack uses an existing vulnerability in a program to grant elevated privileges to a user, or to grant access to information reserved for other programs/users. A well-known example of this is jailbreaking, where a system’s normal limitations on what a user can do are circumvented. Privilege escalation allows an attacker to run programs or access information of another program when they normally couldn’t. In our example, a privilege escalation attack on the control PC could allow an attacker to have administrative permissions, allowing them to turn off camera feeds or disable security notifications while bypassing user authentication. Memory encryption, the principle of least privilege, and keeping software up to date are ways of mitigating privilege escalation attacks.
Physical attacks: playing it cool.
An example of a physical attack would be a cold boot attack. In such an attack, the attacker freezes a system’s RAM modules to preserve their contents longer, then reboots it using their own operating system. The goal of such an attack is to dump the memory contents, effectively turning it into Data at Rest where it can be analyzed for valuable information such as encryption keys. In our example, a successful cold boot attack on the remote PC could result in an attacker gaining information they need to pose as a legitimate remote PC on another system (spoofing), granting them access to the server/database while bypassing user authentication. System configuration checks, memory encryption, and tamper evidence/response are all options for protecting against physical attacks.
Don’t get used.
When you use the proper security measures in your computer systems, you can prevent your data from being targeted or used maliciously. This may be our final installment in our series of blogs covering an Introduction to Secure Data, but data security doesn’t stop here. Just as attackers will always look for new ways to attack your systems, data security is an ongoing effort that requires constant diligence. That’s why Crystal Group continually helps customers in rugged applications protect their hardware, components and data from security attacks.